What is a Reverse Proxy Server?
A Reverse Proxy Server is a component deployed in front of your Web or Application servers, which looks like a web server to the clients (browser, mobile apps) and looks like a browser to the web servers behind it. At the basic level, it intercepts app requests and hides internal hostnames and IP addresses from public view, forwarding (or proxying) requests to the servers behind it.
More advanced reverse proxies can also inspect traffic and provide Web Application Firewall (WAF) functionality. Furthermore, a Reverse Proxy Server typically also supports load balancing and failover between a number of backend servers, providing enhanced availability, as well as better uptime and performance to clients.

Reverse Proxy Server by Ceptor
Ceptor Gateway is a Reverse Proxy Server, which includes an API Gateway, a Web Application Firewall, and a Security Enforcement Endpoint
Ceptor Gateway ensures:
- Only the applications a user is supposed to use are available that user
- Availability of applications by throttling requests so they are not overloaded (throttling can be done per application server instance, per user, per client IP or using any custom attribute or script to decide).
- Security by allowing invalid requests to be filtered out (e.g. POST or query parameters can be configured to require specific patterns or character sets).
- Advanced control over authorization, supporting Role-Based Access Control (RBAC) as well as Attribute-Based Access Control (ABAC).
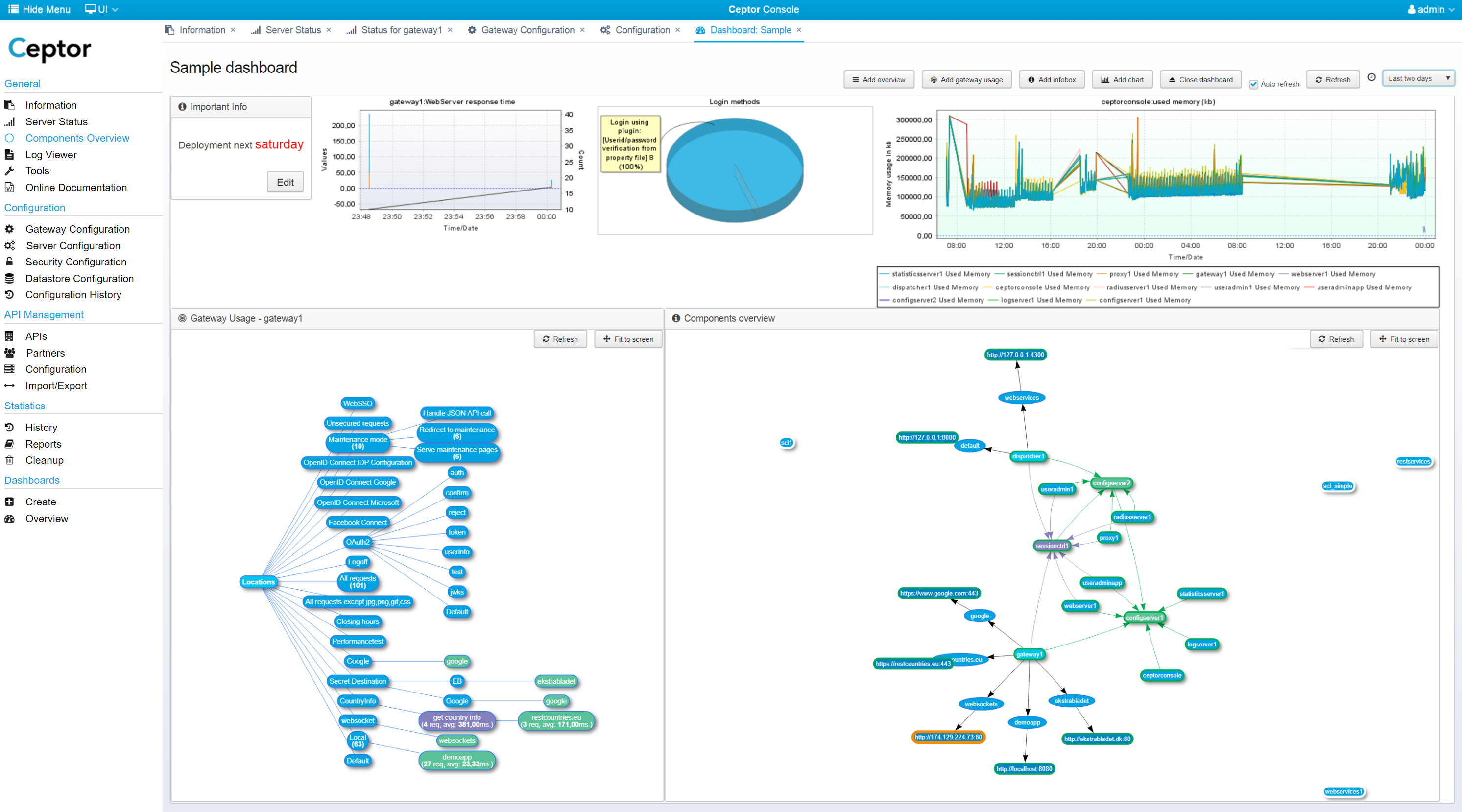
Using Ceptor Console, you can get detailed dashboards providing comprehensive overviews of your system and status.
Use Cases for Ceptor Gateway
Ceptor Gateway is often used as a Reverse Proxy Server that is extended with more complex Authentication and/or Authorization functionality.
- Add two-factor authentication.
- Ensure encryption of traffic
- Protect access to applications, limited by authorization rules defined either in the gateway itself or in ACLs defined in Ceptor user-repositories / data stores.
- Limit concurrent requests or requests per second to protect application/web servers by throttling traffic for resource-hogging clients
- Provide comprehensive Authorization on the URL level.
- Execute application logic, using "Pipelines and Tasks"
- Provide full API Gateway capability. Learn more about Ceptor API Gateway
For deeper insight see our Detailed Feature List
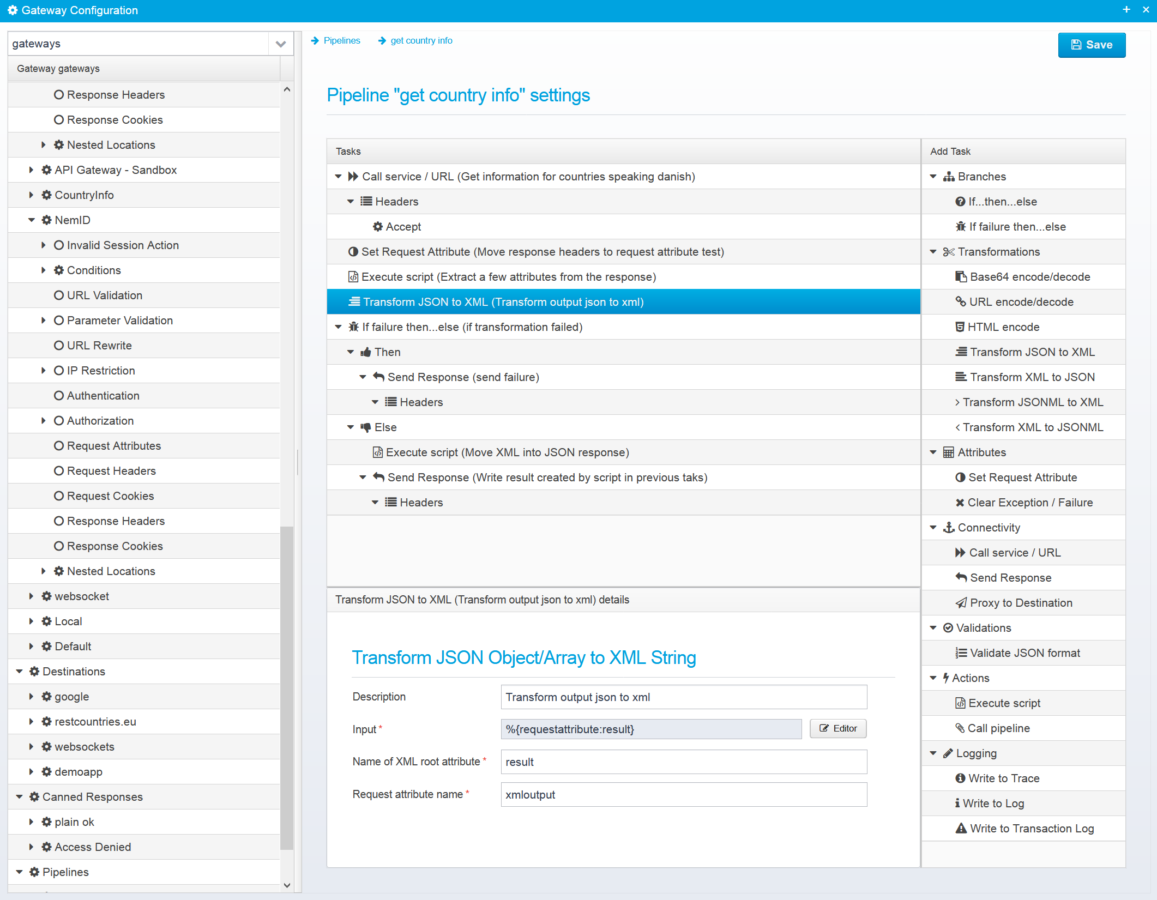
Pipelines and Tasks
Drag tasks together to perform actions
One of the more advanced features available within Ceptor Gateway, is the Enterprise Service Bus (ESB) – like functionality that allows you to drag tasks together to perform actions, such as:
- Calling remote services
Perform an HTTP request to call a service, or retrieve data from a resource - Transform content from XML to JSON and back and combine responses from multiple different requests into one
- Execute script
Allows the script to do any processing it wants by running custom code. - Call pipeline
Call another pipeline and run through all its tasks - this allows you to chain pipelines and reuse collections of tasks from other pipelines.
Secure Web and Application Servers
Access to specific applications / URLs can be protected by complex authorization rules and any form of authentication, such as:
- OpenID Connect / OAuth 2
- SSL Client Certificate
- Bearer Token
- API key
- SAML Identity Federation
- SPNEGO / Kerberos
Many more are available, both out of the box and provided via scripting. APIs and plugins make it easy to extend the functionality with additional authentication methods.
OpenID Connect
Ceptor can act as both an OpenID Provider, federating identities to third parties using the OpenID Connect Protocol, and it can act as a Resource Owner, authenticating users against other OpenID providers - e.g.
- Microsoft
- Any OpenID Provider, which supports the OpenID Connect Specification.
This configuration example shows how to configure Ceptor Gateway to rely on Microsoft to authenticate a user.
Attribute-Based Access Control (ABAC)
In addition to the simpler Role-Based Access Control (RBAC) – Ceptor also support ABAC, allowing you to based authorization decisions upon individual attributes within a request. Sometimes this functionality is also referred to as “Context Based Authorization” – where access decisions is taken based upon request attributes and user context, ABAC allows you to create rules that do not just allow a user to access a given functionality based upon role membership, but also based checking on e.g. time of day, customer ID used etc.
Detailed Feature List
Ceptor Gateway has amongst other, this functionality:
Reverse Proxy Server Functionality
- HTTP 1.0, 1.1 and 2 support - both for client and servers
- HTTP/HTTPS/AJP Listeners
- SSL/TLS SNI
- WebSocket support
- HTTP/2 PUSH
- HTTP/2 Upgrade and ALPN
- Proxy Protocol support
- Response compression
- Location-based configuration
- Matching based upon host, path, cookie, query, post params, request method, scheme, headers, remote IP, attributes, GeoIP, userid, usergroup, pathparam, script
- URL Rewriting
- Proxy forwarding
- Full access log functionality with configurable content
- Destination / Target servers
- Authentication with servers
- Basic Auth
- Bearer Token
- SPNEGO/NTLM/Kerberos
- Forward SSL Client cert
- SAML Web SSO
- LTPA Tokens
- Stickiness
- Ping servers
- Customize request method URI
- Configure expected response codes
- Response body checking script
- Authentication with servers
- Request/response modification
Web Application Firewall
- URL validation
- Request parameter (query, path, post) validation
- HTTP Header rewriting/adding/removal
- Cookie rewriting/adding/removal
- Session cookie SameSite support
API Gateway Functionality
- Rate limiting for API calls
- Multiple subscription levels
- Multiple limits, e.g. 100 per minute, max 10 per second
- Plugins for implementing own limits and rules
- Pipelines and Tasks
- XML to JSON / JSON to XML conversion
- Encoding / decoding
- Aggregate service calls
- Full scripting and flexibility
- Logging / tracing
- JSON Validation
- Serve published APIs for multiple environments
Authentication and Authorization
- Session resolvers
- Advanced IP Address change filtering
- IP ranges
- GeoIP information
- Advanced scripting
- Domain redirect (share session between multiple separate domains)
- Authentication
- SSL Client certificate
- Basic Auth
- Bearer Token
- NTLM
- SPNEGO/Kerberos
- Forms
- OAuth / OAuth 2.0
- OpenID Connect
- ADFS / Web SSO
- LTPA Tokens
- Advanced script-based authentication - allows you to script any form of authentication
- Optional use of separate Login Application
- Authorization
- Role-Based Access Control (RBAC)
- Attribute-Based Access Control (ABAC)
- Authorization scripts for advanced checking
OpenID Connect Provider
- OpenID Connect Discovery
- JSON Web Key Set (JWKS) URI / Metadata
- Authorize / Token endpoints
- UserInfo endpoint
- Token Introspection (RFC7662)
- Token Revocation (RFC7009)
Request Throttling
- Request Queuing / Throttling
- Limit concurrent requests
- Max requests per second
- Limits can be qualified, e.g. by IP address, client ID etc.
- Response Throttling
- Max bytes per second
Advanced Functionality
- Java or JavaScript / Python / Groovy based plugins and scripts
- CookieSnapper - hide cookies from browsers
- Request tracing
- "Canned" responses
- Serve static resources
Contact us